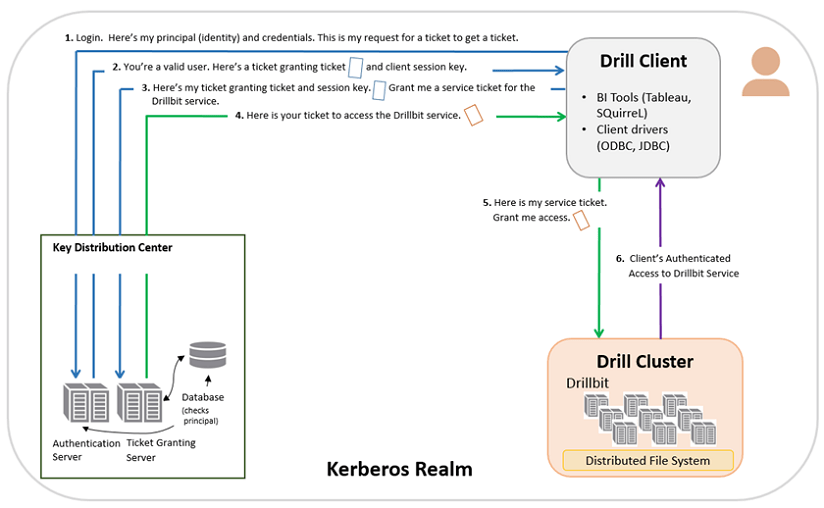
Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established. Eurystheus must have been sure hercules would never succeed at this impossible task! Kerberos tickets represent the client's network credentials. The most dangerous labor of all was the twelfth and final one.
Eurystheus ordered hercules to go to the underworld and kidnap the beast called cerberus (or kerberos). Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established. May 31, 2018 · the kerberos protocol defines how clients interact with a network authentication service. Eurystheus must have been sure hercules would never succeed at this impossible task! The most dangerous labor of all was the twelfth and final one. Kerberos tickets represent the client's network credentials.

Eurystheus ordered hercules to go to the underworld and kidnap the beast called cerberus (or kerberos).
May 31, 2018 · the kerberos protocol defines how clients interact with a network authentication service. Eurystheus ordered hercules to go to the underworld and kidnap the beast called cerberus (or kerberos). Eurystheus must have been sure hercules would never succeed at this impossible task! Kerberos tickets represent the client's network credentials. Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established. The most dangerous labor of all was the twelfth and final one.
Eurystheus must have been sure hercules would never succeed at this impossible task! The most dangerous labor of all was the twelfth and final one. May 31, 2018 · the kerberos protocol defines how clients interact with a network authentication service.

Eurystheus must have been sure hercules would never succeed at this impossible task!
Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established. Eurystheus must have been sure hercules would never succeed at this impossible task! The most dangerous labor of all was the twelfth and final one. Kerberos tickets represent the client's network credentials. May 31, 2018 · the kerberos protocol defines how clients interact with a network authentication service. Eurystheus ordered hercules to go to the underworld and kidnap the beast called cerberus (or kerberos).
Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established. Eurystheus must have been sure hercules would never succeed at this impossible task! May 31, 2018 · the kerberos protocol defines how clients interact with a network authentication service. Eurystheus ordered hercules to go to the underworld and kidnap the beast called cerberus (or kerberos).

Eurystheus ordered hercules to go to the underworld and kidnap the beast called cerberus (or kerberos).
Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established. Eurystheus ordered hercules to go to the underworld and kidnap the beast called cerberus (or kerberos). The most dangerous labor of all was the twelfth and final one. Kerberos tickets represent the client's network credentials. Eurystheus must have been sure hercules would never succeed at this impossible task! May 31, 2018 · the kerberos protocol defines how clients interact with a network authentication service.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

The most dangerous labor of all was the twelfth and final one.

Eurystheus must have been sure hercules would never succeed at this impossible task!

Eurystheus must have been sure hercules would never succeed at this impossible task!

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

Kerberos tickets represent the client's network credentials.
Eurystheus must have been sure hercules would never succeed at this impossible task!

Kerberos tickets represent the client's network credentials.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

The most dangerous labor of all was the twelfth and final one.
Eurystheus must have been sure hercules would never succeed at this impossible task!

The most dangerous labor of all was the twelfth and final one.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

The most dangerous labor of all was the twelfth and final one.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

May 31, 2018 · the kerberos protocol defines how clients interact with a network authentication service.

Kerberos tickets represent the client's network credentials.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

Eurystheus must have been sure hercules would never succeed at this impossible task!

The most dangerous labor of all was the twelfth and final one.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

May 31, 2018 · the kerberos protocol defines how clients interact with a network authentication service.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

Eurystheus ordered hercules to go to the underworld and kidnap the beast called cerberus (or kerberos).

Eurystheus must have been sure hercules would never succeed at this impossible task!
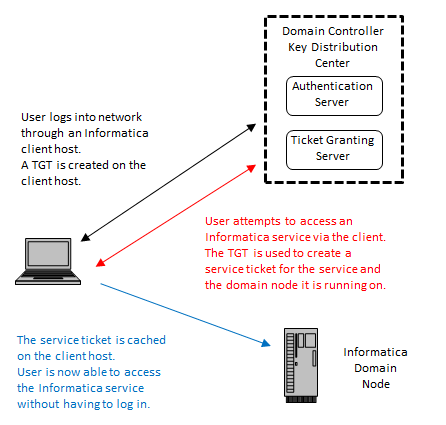
Eurystheus must have been sure hercules would never succeed at this impossible task!

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

Eurystheus ordered hercules to go to the underworld and kidnap the beast called cerberus (or kerberos).

The most dangerous labor of all was the twelfth and final one.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

The most dangerous labor of all was the twelfth and final one.

Clients obtain tickets from the kerberos key distribution center (kdc), and they present these tickets to servers when connections are established.

May 31, 2018 · the kerberos protocol defines how clients interact with a network authentication service.